library
Image generated using ChatGPT. Image of a futuristic city powering personal tech devices, cars, tractors and drones with 6G. Later retouched. November 4, 2025.
We rarely think about the invisible infrastructure that keeps us connected — until it fails. Whether it's a dropped call during an emergency, a delayed text from a loved one, or a network outage that halts business operations, the mobile wireless network is more than just a convenience. It’s a critical backbone of modern life.
However, beyond powering our daily communications, this network plays a far more strategic role. It underpins emergency response systems, supports industrial automation, and safeguards national defense operations. As we look ahead to the next generation of wireless — 6G — the stakes are rising.
6G won’t just connect devices; it will sense, localize, and interpret the world around us in real time. This convergence of sensing and communications will rely on hardware, software, and data pipelines that process detailed and potentially sensitive environmental and behavioral information, allowing it to unlock powerful new capabilities — and expose new vulnerabilities. If key components or platforms are controlled by foreign or untrusted entities, it opens the door to surveillance, manipulation, or disruption. In this high-stake environment, ensuring independent control over the full supply chain — from chipsets to cloud — will be critical to protecting national security, data integrity, and technological independence.
Digital sovereignty is the ability of a country to control its own digital infrastructure, data, and technologies without being overly reliant on foreign powers. With the coming convergence of sensing and communications, digital sovereignty in 6G is an essential cornerstone of protecting our communications and personal data.
The Threat Landscape
The threats to telecom networks are no longer theoretical. Malicious actors often use SIM cards or VoIP accounts en masse to spread misinformation, conduct phishing attacks, or commit fraud. In September 2025, thousands of rogue devices were discovered in New York City, suspected of being part of a coordinated denial-of-service attack or a fraud network. Incidents like the massive AT&T data leak in 2024 have shown that network vulnerabilities can be heavily exploited to track users, steal data, and disrupt services. When a country outsources the design and manufacturing of its telecom infrastructure, it loses visibility into how that infrastructure operates — and with it, the ability to detect or mitigate hidden backdoors or security flaws.
A Shift in Global Power
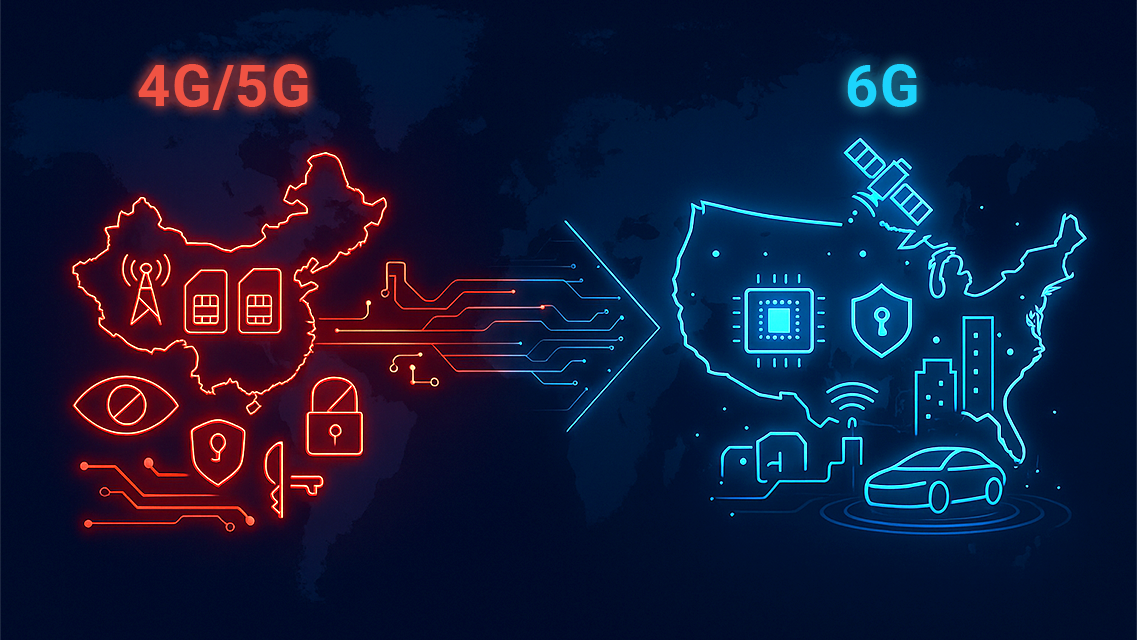
In the early days of mobile technology, the United States and Europe led the way. But with the rollout of 4G/LTE, China surged ahead, capturing a significant share of the global telecom market. This shift has elevated the risk to Western nations for maintaining control over their networks and defending against emerging threats.
As a result, governments around the world are taking action.
In the United States, the Secure and Trusted Communications Network Act restricts the use of telecom equipment from high-risk vendors, while the CHIPS and Science Act provides funding to boost domestic innovation in semiconductors and telecom technologies, including Open Radio Access Network (O-RAN). Although O-RAN adoption remains limited, this policy push has inspired both startups and established players to build a dynamic open ecosystem through value-driven partnerships.
Across the Atlantic in the European Union, the EU Toolbox for 5G Security encourages member states to reduce reliance on high-risk vendors and instead invest in indigenous 6G development.
In Asia, Japan and South Korea, and India are pushing the boundaries of 5G and 6G, while also supporting local telecom giants like NEC, Fujitsu, and Samsung. India, a long-standing leader in telecom services and devices, is now capable of delivering a full-stack indigenous solution.
Industry Response and the Role of Startups
The evolution of 5G — and the emergence of 6G — is now accelerating at the pace of software. Policy initiatives aimed at opening mobile wireless networks and demands to address new markets have empowered software-driven and private 5G providers to integrate with traditional telecom players to accelerate their time to deployment and enhance security of the network. Providers of network API layers and 5G core software are already providing enhanced security to mobile wireless networks. New software-focused companies are revitalizing and reshoring SIM card provisioning through cloud-based eSIM platforms, reversing decades of offshoring and industry decline. This enables enterprises and governments to deploy networks with greater trust, flexibility, and control. As industry responds to these policy signals, a more diverse and collaborative ecosystem is emerging where startups and established players can co-develop software solutions that open new markets and deliver more secure, resilient networks. On the hardware front, innovators such as NVIDIA and others continue to lead the market by integrating AI and communications and pushing towards software-defined hardware architectures for flexible and secure solutions. These U.S.-lead innovations foster trusted supply chains, enabling greater security of our critical communications infrastructure.
Digital Sovereignty in the 6G Era
From IQT’s perspective, the convergence of sensing and communication is a double-edged sword: it unlocks new dimensions of connectivity and intelligence, but also heightens the stakes for privacy, security, and strategic autonomy. Without strong digital sovereignty, nations and enterprises risk ceding control over this sensitive data to foreign infrastructure providers or opaque cloud ecosystems. Ensuring domestic control over the full supply chain — from chipsets to cloud, and from algorithms to operational know-how — will be essential to harness the benefits of ISAC while safeguarding national security and data integrity. While 6G is still under development, now is the time to invest in advanced research, foster a home-grown supply chain, and build the workforce that will power and secure the next generation of wireless. As 6G brings new capabilities like digital twinning, AI-native networks, flexible hardware architectures, and real-time environmental awareness, the countries that invest in sovereignty today will be better equipped to protect their economies, their citizens, and their democratic institutions.



