
Some Context
Secure Agile Operations (SAO) is the ability of a distributed workforce to securely access critical data and services from anywhere at any time. The pandemic created an acute inflection point for enterprises to not only expand remote work, but to layout a permanent shift to all-remote for a significant percentage of their workforce. Many enterprise buyers now find themselves scouring the market for technologies that enable agile and secure distributed work for their enterprise.
IT leaders are asking how to best secure their distributed systems as they adopt remote work policies. To answer that question, there are two broad considerations for leaders to consider:
- The gap between on-premises, legacy systems, and commercial cloud IT is growing. Companies are accelerating their digital transformation by increasing their use of SaaS and other associated cloud native technologies. In this world, best-of-breed security companies will focus their efforts on solving a newer class of problems that cloud native infrastructure presents. In time these vendors will be less willing to build products that address the myriad of problems linked to keeping alive a patchwork of neglected legacy, on-premises systems.
- The attack surface is changing and expanding. A dynamic workforce operating from various locations and endpoints introduces considerable information assurance problems. Security is a lot harder when the attack surface – the culmination of all the networks and endpoints and systems organizations rely on – change and expand dramatically.
With those considerations in mind, SAO attempts to make real the otherwise confusing and amorphous concept known as Zero Trust. Depending on who you ask Zero Trust has different definitions. We see Zero Trust as an operating principle that calls for the design and use of computing systems under an assumption of breach. An assumed breach mindset requires engineering teams, compliance officials, and executives to embrace entirely new ways of implementing safeguards for their IT infrastructure. To effectively transition to this paradigm, IT leaders have to tackle the cultural issues that beset their organizations today and challenge conventional thinking around topics like trust, identity, and risk.
Challenges & Opportunities
As we see it, there are three big challenges SAO initiatives need to address:
- Dissolving perimeter. Network security used to be pretty straightforward where we had a clear boundary that we drew around our offices, users, and on-premises applications. Securing that network centered on placing a firewall at the perimeter and separating your internal enterprise resources from the external open internet. If you did a good enough job you could say that your network was secure. That was then, but now applications are everywhere. They cross boundaries between mobile and desktop, on-premises and cloud. With most internet traffic is encrypted and data spread across owned and leased infrastructure, enterprise security teams are attempting to protect all the data, in all the places, while wearing a blindfold… a daunting challenge indeed.
- A massive shift in corporate work models. Today’s workforce demands remote access to data and communication systems that allow real-time collaboration. In response, enterprise has accelerated its adoption of SaaS products hosted in the public cloud to keep their workforce productive and satisfied. Organizations that have not adjusted to this operating model will experience difficulty in attracting or obtaining talent because the IT and security roadblocks that have historically kept employees from accessing the data they need is no longer acceptable in today’s new normal.
- Support for large, monolithic legacy apps has become increasingly hard to find. Legacy systems are being left behind as new application architectures move to break monolith applications down into microservices, taking software deployment cycles from months-long ordeal down to a matter of hours. The future belongs to those who embrace these new architectural approaches. Leaving those who resist it in the dust.
There’s tremendous opportunity in tackling these three challenges:
- Flexibility. Organizational transformation for employees to access data and work collaboratively, all while enforcing precisely who is and isn’t allowed access to a digital resource down to a single API or data point, is possible through an empirical analysis of users, machines, and data.
- Efficiency. Realize the benefits of an efficient system that offers consistent access to large datasets kept on the open internet, along with low-side development and high-side integration service for government agencies. We believe there’s efficiency-producing technologies out there that make the query-in-place aspects of this problem addressable, unlocking new real-time collections and analysis capabilities without the need for data duplication or concerns about sharing sensitive information with third parties.
- Resiliency. What about building infrastructure that is resilient enough to withstand outages by rapidly deploying new compute resources as conditions and workloads shift? This level of resiliency is certainly possible, given the emergence of software systems employing chaos engineering concepts that push themselves to build greater levels of confidence and objectivity in their ability to withstand turbulent and unexpected conditions.
We believe that gains in flexibility, efficiency, and resiliency are within reach if enterprise undertakes what the security community has colloquially referred to as the Zero Trust journey. A journey which calls for understanding today’s fundamental shift in trust model.
Shifting Trust Models
For over 30 years, IT has relied on perimeter-based models to defend the enterprise. This model places network level boundaries between what is on the Internet and what is on a trusted network. It confers trust onto users and devices allowing them to operate within the network boundary unabated. This implicit trust presents a great deal of risk because once inside a trusted zone, there are typically few security controls to protect other users and devices connected to that same network. The fallacy of conferring implicit trust to users and devices because of where they are on a network plane has been questioned for a long time. But recently, we see in the market an alternative model based on identity supplanting it.
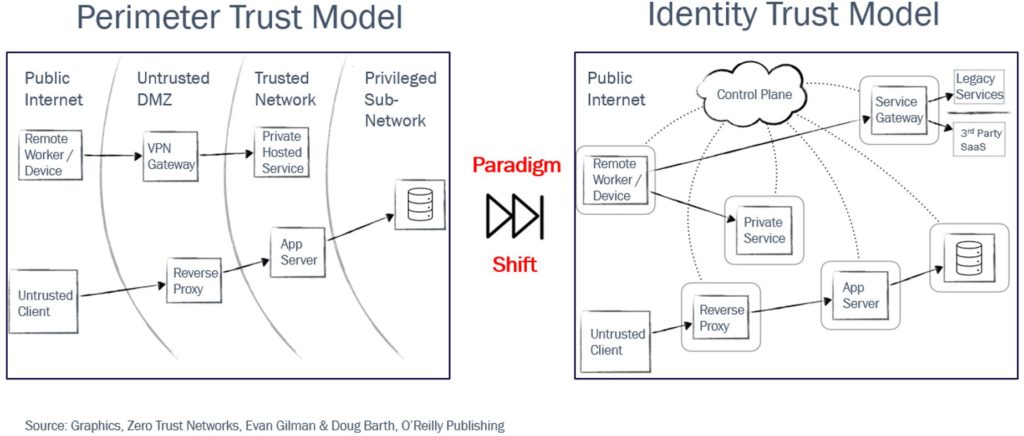

The identity-based model is an approach that controls access to data or services based on the authenticated identity of a user or a device. This allows organizations to grant access in a way that that ensures an accurate match between what users are entitled to and what they actually receive. This model also has the ability to consider other attributes like device location and third-party risk information when making decisions about allowing users access to a resource.
Within the security community there is wide agreement that perimeter-based security models are on their way out and identity-based models are in (see Figure 1). But getting there in a brown field environment is tough, especially for enterprises with large networks and tons of legacy applications. This is a journey where culture, as much as technology, has a role to play. Because whatever solution technologists propose to move their organizations from perimeter to identity, we need to understand that rip and replace is in many cases not an option. Unfortunately, when commercial vendors, market analysts, and inexperienced engineers talk about this shift as an “all or nothing” affair, they can actually make organizations hesitant to begin their journey. However, failing to undertake this journey comes with consequences.
What We See
Sole reliance on perimeter-based trust models will lead to more security breaches. We know this because almost every significant breach over the last 10 years can be traced back to the abuse of implicit trust inherit in perimeter-based security controls. As the perimeters continue to dissolve, we should expect more incidents of malicious actors using opensource tools like Mimikatz and Cobalt Strike to move laterally inside of corporate networks in an effort to steal sensitive information and, in some cases, even destroy enterprise infrastructure via ransomware attacks.
Also troubling is insecure cloud migration accelerated by the pandemic driven by a workforce demanding access to data and services through SaaS platforms hosted in the public cloud. Figure 2 highlights this shift was well underway before COVID and continues at breakneck speed.
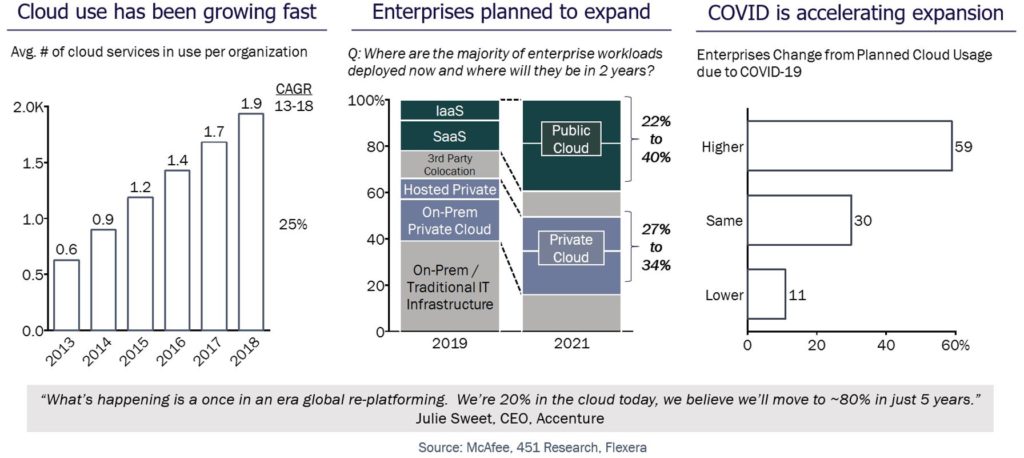

The left-hand side of Figure 2 shows a 25% year-over-year growth in cloud services by enterprise since 2013. The middle graphic forecasted that in 2019 enterprise use of public cloud would double by 2021. Now, in direct response to the pandemic lockdowns, we are seeing that nearly 60% of all enterprises are expected to increase their usage of the cloud beyond that doubling rate. We are truly in an era of re-platforming where enterprises that do not make the migration to cloud securely risk everything.
As enterprises are running to SaaS, we are seeing the increased usage of these platforms leaving legacy systems behind. Enterprise development teams are using the migration as an opportunity to change application architectures away from monolith to microservice approaches. From a network perspective, this means there are a lot more connections and for enterprises that seek to embrace the cloud, their identity and access management systems are going to become increasingly more complex and difficult to manage. As this ecosystem looks less like traditional on-prem infrastructure, the more we expect solutions to be geared towards solving the problems of this new ecosystem while innovative technology that supports bare metal, legacy infrastructure will start to fall by the wayside.
Some Thoughts
Given what we have seen with respect to breaches, shifting work models accelerated by the cloud, and enterprise adoption of SaaS, it becomes clear that the operating model of tomorrow is here today. Provided employees have broadband internet, use of a mobile device, and access to end-to-end encrypted collaboration apps, we will continue to see companies embrace a future where talent can work from anywhere. We believe the future belongs to those that are able to stitch together these technologies to realize the full potential of SAO:
- Endpoint. Introspection up and down the stack with special attention paid to the areas of firmware and hardware integrity is a critical first step in building a real Zero Trust capability for any organization. Given the dearth of market activity taking place in those areas compared with security offerings at the application layer, and as attacks continue to move down the stack, our team views this space as ripe for innovation and early stage investment. Expect us to follow firmware and hardware integrity closely.
- Data Security. Here our focus is on classes of technology that allow for computation over encrypted data, like partially/fully homomorphic encryption, secrets sharing, and privacy-preserving approaches that facilitate federated learning. The goal here is to complete the triad of ensuring encryption in transit, at rest, and in use.
- Identity + Entity Management. Identity is the linchpin of any informed Zero Trust architecture. We believe continuous attestation of users as well as machines is needed to show proof that the user is who they say they are and (that at every layer of the stack) the device that is trying to communicate is what it says it is based on validation of its current running state against what we believe to be known good. Also of interest are technologies that can manage the identity lifecycle of an enterprise’s workforce in an automated way to limit errors and accumulation of standing privileges over time.
- Network Fabric. Virtualization of the network has created the potential for numerous security gains by allowing enterprises to isolate, segment, and steer traffic in ways that they never could before. On top of this software defined infrastructure, our team has seen the potential for a new generation of network security tools to push the envelope by creating access gateways that can intelligently analyze risk in a probabilistic way as they make decisions about allowing or denying sessions that connect users to internally hosted applications and sensitive data. These gateways will continuously provide mutual authentication for people and machines while being underpinned by orchestration platforms like Kubernetes.
- DevOps-Oriented Infrastructure. Designing for SAO means empowering software developers to operate more effectively. We believe enterprise should actively seek out and implement technologies that allow DevOps teams to exercise greater control over their workflows as they build software on the open internet and later securely deploy what they have built onto sensitive internal networks. Efforts to make life easier on development staff almost always pays dividends in the form of faster release cycles, more features, and greater levels of integration with legacy systems. In this area we see bill of materials, scalable fuzz and test platforms, and tools that inform enterprise about the provenance and pedigree of the code they rely on as crucial to building a SAO capability that squashes technical debt and withstands the test of time.
If you are a founder, engineer, or thinker building any of these technologies, reach out to us. We would like to learn more. If you are a government IT leader who is thinking about these problems and want SAO, reach out to us. We love to commiserate.

